This section discusses the following topics:
A virtual private network securely extends a private intranet across a public network such as the Internet. VPNs convey information across what is essentially a private tunnel through the Internet to and from remote users, branch offices, and business partners/suppliers. Companies can opt for Internet access through Internet service providers (ISPs) using direct lines or local telephone numbers and eliminate more expensive leased lines, long-distance calls, and toll-free telephone numbers.
A recommended resource for planning the implementation of a VPN is Chapter 9 of A Comprehensive Guide to Virtual Private Networks, Volume III, ISBN SG24-5309-00. This information is also available on the Internet World Wide Web at http://www.redbooks.ibm.com. Several additional resources are available when you search the Web for "VPN" or "virtual private network."
The operating system uses IP Security, which is an open, standard security technology developed by the Internet Engineering Task Force (IETF), as an integral element of IBM SecureWay VPN solutions. IP Sec provides cryptography-based protection of all data at the IP layer of the communications stack. It provides secure communications transparently. No changes are needed for existing applications. IP Sec is the IETF-chosen industry standard network security framework for both the IP Versions 4 and 6 environments.
IP Security protects your data traffic using the following robust cryptographic techniques:
Authentication algorithms prove the identity of the sender and data integrity by using a cryptographic hash function to process a packet of data (with the immutable IP header fields included) using a secret key to produce a unique digest. On the receiver side, the data is decapsulated using the same function and key. If either the data has been altered or the sender key is not valid, the datagram is discarded.
Encryption uses a cryptographic algorithm to modify and randomize the data using a certain algorithm and key to produce encrypted data known as cyphertext. Encryption makes the data unreadable while in transit. Once received, the data is recovered using the same algorithm and key (with symmetric encryption algorithms). Encryption must occur with authentication to verify the data integrity of the encrypted data.
These basic services are implemented in IP Sec by the use of the Encapsulating Security Payload (ESP) and the Authentication Header (AH). With ESP, confidentiality is provided by encrypting the original IP packet, building an ESP header, and putting the cyphertext in the ESP payload.
The AH can be used alone for authentication and integrity checking if confidentiality is not an issue. With AH, the static fields of the IP header and the data have a hash algorithm applied to compute a keyed digest. The receiver uses its key to compute and compare the digest to make sure the packet is unaltered and the sender's identity is authenticated.
The IP Security feature of this operating system provides the following functions:
The following features are available with Internet Key Exchange, AIX 4.3.2 and later:
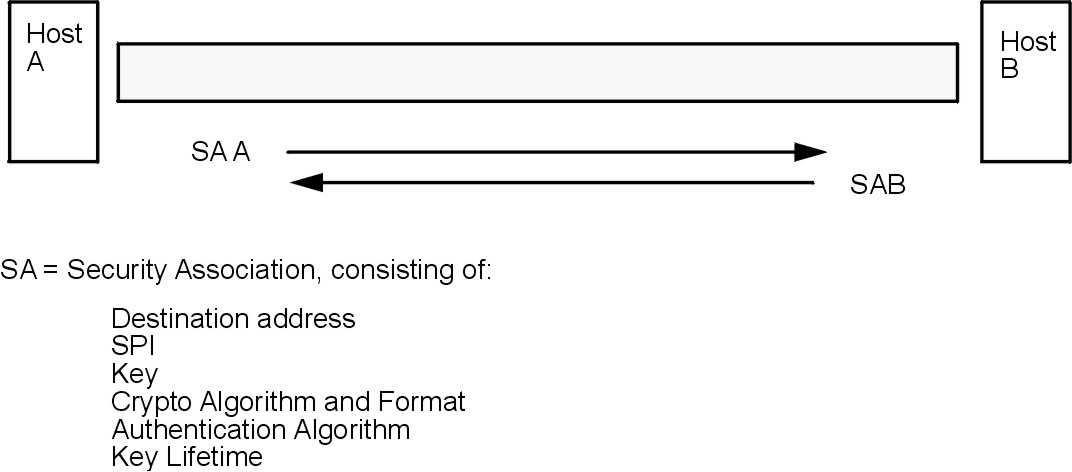
The building block on which secure communications is built is a concept known as a security association. Security associations (SAs) relate a specific set of security parameters to a type of traffic. With IP Security-protected data, a separate SA exists for each direction and for each header type, AH or ESP. The information contained in the SA includes the IP addresses of the communicating parties, a unique identifier known as the Security Parameters Index (SPI), the algorithms selected for authentication and/or encryption, the authentication and encryption keys, and the key lifetimes figure.
Figure 4-1. Establishment of a Secure Tunnel Between Hosts A and B. This illustration shows a vurtual tunnel running between Host A and Host B. Security Association (SA) A is an arrow directed from Host A to Host B. SA B is an arrow directed from Host B to Host A. A Security Association consists of the Destination Address, SPI, Key, Crypto Algorithm and Format, Authentication Algorithm, and Key Lifetime.
 |
The goal of key management is to negotiate and compute the SAs that protect IP traffic.
To set up a secure communication between two hosts, Security Associations must be negotiated and managed during the use of the tunnel. Two types of tunnels are supported, and each uses a different key management technique:
IKE Tunnels are based on the ISAKMP/Oakley standards developed by the IETF. With this protocol, security parameters are negotiated and refreshed, and keys are exchanged securely. Two types of authentication are supported: preshared key and X.509v3 digital certificate signatures.
The negotiation uses a two phase approach. The first phase
authenticates the communicating parties, and specifies the algorithms to be
used for securely communicating in phase 2. During phase 2, IP Security
parameters to be used during data transfer are negotiated, security
associations and keys are created and exchanged.
| Algorithm | AH IP Version 4 & 6 | ESP IP Version 4 & 6 |
|---|---|---|
| HMAC MD5 | X | X |
| HMAC SHA1 | X | X |
| DES CBC 8 | X | |
| Triple DES CBC | X | |
| ESP Null | X |
Manual tunnels provide backward compatibility and interoperate with
machines that do not support IKE key management protocols. The
disadvantage of manual tunnels is that the key values are static. The
encryption and authentication keys are the same for the life of the tunnel and
must be manually updated.
| Algorithm | AH IP Version 4 | AH IP Version 6 | ESP IP Version 4 | ESP IP Version 6 |
|---|---|---|---|---|
| HMAC MD5 | X | X | X | X |
| HMAC SHA1 | X | X | X | X |
| Triple DES CBC | X | X | ||
| DES CBC 8 | X | X | ||
| DES CBC 4 | X | X |
Since IKE tunnels offer more effective security, IKE is the preferred key management method.
Note: Beginning with AIX 4.3.3, CDMF support has been removed because DES is now available world wide. Reconfigure any tunnels that use CDMF to use DES or Triple DES.
Filtering is a basic function in which incoming and outgoing packets can be accepted or denied based on a variety of characteristics. This allows a user or system administrator to configure the host to control the traffic between this host and other hosts. Filtering is done on a variety of packet properties, such as source and destination addresses, IP version (4 or 6), subnet masks, protocol, port, routing characteristics, fragmentation, interface, and tunnel definition.
Rules, known as filter rules, are used to associate certain kinds of traffic with a particular tunnel. In a basic configuration for manual tunnels, when a user defines a host-to-host tunnel, filter rules are autogenerated to direct all traffic from that host through the secure tunnel. If more specific types of traffic are desired (for instance subnet to subnet), the filter rules can be edited or replaced to allow precise control of the traffic using a particular tunnel.
For IKE tunnels, the filter rules are also automatically generated and inserted in the filter table once the tunnel is activated.
Similarly, when the tunnel is modified or deleted, the filter rules for that tunnel are automatically deleted, which greatly simplifies IP Security configuration and helps reduce human error. Tunnel definitions can be propagated and shared among machines and firewalls using import and export utilities, which is especially helpful in the administration of a large number of machines.
Filter rules associate particular types of traffic with a tunnel, but data being filtered does not necessarily need to travel in a tunnel. This aspect of filter rules lets the operating system provide basic firewall functionality to those who want to restrict traffic to or from their machine in an intranet or in a network that does not have the protection of a true firewall. In this scenario, filter rules provide a second barrier of protection around a group of machines.
Once the filter rules are generated, they are stored in a table and loaded into the kernel. When packets are ready to be sent or received from the network, the filter rules are checked in the list from top to bottom to determine whether the packet should be permitted, denied, or sent through a tunnel. The criteria of the rule is compared to the packet characteristics until a match is found or the default rule is reached.
The IP Security function also implements filtering of non-secure packets based on very granular, user-defined criteria, which allows the control of IP traffic between networks and machines that do not require the authentication or encryption properties of IP Security.
IP Security supports the use of X.509 Version 3 digital certificates. The IBM Key Manager tool manages certificate requests, maintaining the key database, and other administrative functions.
Digital certificates are described in Digital Certificate Configuration. The IBM Key Manager and its functions are described in Using the IBM Key Manager Tool