There are several mechanism for securing the WAS, for example:
- using operating system users (securing via local OS)
- using an LDAP directory.
This scenario illustrates authentication against an LDAP directory.
This task requires input relative to an LDAP user which must already exist in the LDAP directory and must have been created with specific rights. In our scenario, we used the wpsadmin user set up earlier when configuring a typical LDAP server. You will be prompted to enter this user id and password when you later start the WebSphere Administrative Console.
For detailed information about this LDAP user, refer to Configuring and Customizing the LDAP Repository.
Alternative Methods for Securing the WebSphere Application Server
To secure your WebSphere Application Server, two alternative methods are available:
- you can use Security tab in the Deployment Wizard for V5 Web Applications
to secure the WAS (with LDAP authentication only) and deploy the
Enterprise Archive file at the same time.
Note: you cannot use the Security tab for the sole purpose of configuring WAS security: clicking the Finish button in the Deployment Wizard for V5 Web Applications also deploys the Enterprise Archive file. Both operations are run together. - or, you can configure security manually using the WebSphere Administrative Console.
Variable
Signification
Server User ID user id that will be used to log onto WebSphere administration console when security will be activated Server User Password password of the LDAP user used to administrate WebSphere Host name of the machine on which the LDAP server is running Port the communication port of the LDAP server Base Distinguished Name Bind Distinguished Name LDAP user having bind privilege Bind Password password of the LDAP user having bind privilege Domain Name domain name <was_install_dir> directory of the WAS installation <admin_user> name of user chosen to administrate WebSphere <admin_password> password of user chosen to administrate WebSphere
Securing the WebSphere Application Server Using the Security Tab
Once that you have started the Deployment Wizard for V5 Web Applications as described in Creating the Enterprise Archive File:
- Select the Security tab:

- Check the Configure WebSphere security
option:
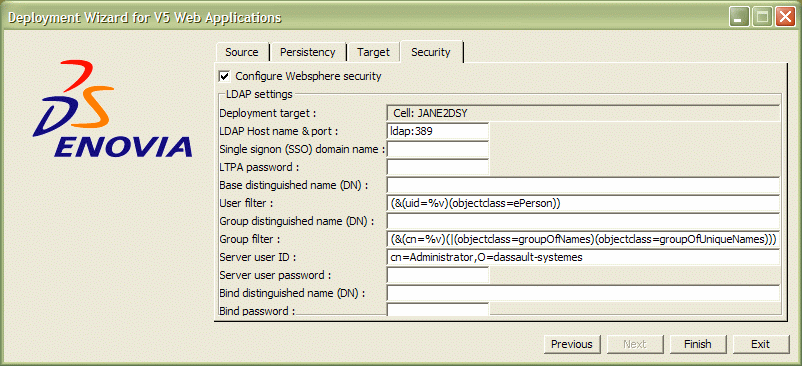
- Provide the required input:
Deployment target: name of cell on machine on which the WAS is running, for example:
Cell: JANE2DSYLDAP Host name & port: name of the machine on which the LDAP server is running, and the LDAP server's port number, separated by a ":" like this:
papouvn2dsy:389Single signon (SSO) domain name: Enter a domain name, for example like this:
dsy.dsLTPA password: To encrypt communications between the WebSphere Application Server and the WebSphere Administrative Console, set the LTPA password as desired. This is the password used to allow a WAS server pool to share the same LTPA Token (refer to the IBM WAS documentation for more details).
Base Distinguished Name (DN): depends on the LDAP server configuration. In our scenario:
cn=users,o=mycompany.orgUser Filter: must be compatible with the LDAP schema. The default value is:
(&(uid=%v)(objectclass=ePerson))Because we imported an LDAP file with
objectclass=Person(described in Configuring and Customizing the LDAP Repository), it should be set to:(&(uid=%v)(objectclass=Person))Group Distinguished Name (DN): depends on the LDAP server configuration. In our scenario:
cn=groups,o=mycompany.orgGroup Filter: must be compatible with the LDAP schema. The default value is:
(&(cn=%v)(|(objectclass=groupOfNames)(objectclass=groupOfUniqueNames)))Because in Configuring and Customizing the LDAP Repository we illustrate an LDAP file for groups with
objectclass==groupOfNamesandobjectclass=groupOfUniqueNames, leave the default value.Server User ID: user id that will be used to log onto the WebSphere Administrative Console once security has been activated. In our scenario:
uid=wpsadmin,cn=users,o=mycompany.orgServer User Password: password of the LDAP user used to administrate WebSphere
Bind Distinguished Name: LDAP user having bind privilege, for example in our scenario:
cn=root
Bind Password: password of the LDAP user having bind privilege.The end result looks something like this:
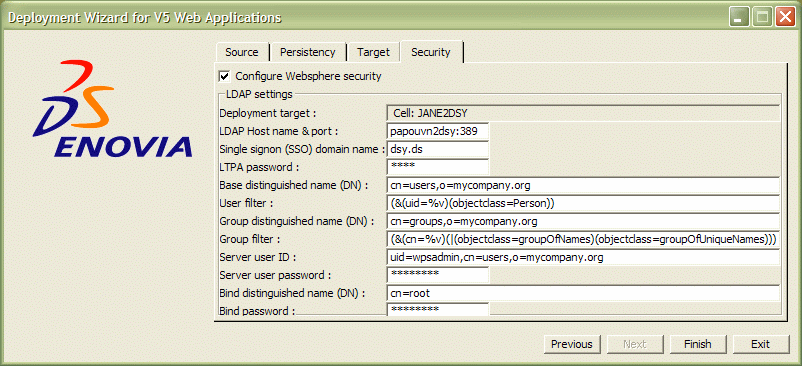
- Click the Finish button.
Note that this both deploys the EAR file and secures the WAS at the same time: you cannot use the wizard for the sole purpose of securing the WAS.
Checking Security Using the WebSphere Administrative Console
Once you have secured the WAS using the Security tab in the Deployment Wizard for V5 Web Applications, you can then start the WebSphere Administrative Console and follow the instructions below to check that the WAS has been correctly secured.
Note: this is not mandatory. All necessary security customizations are performed automatically by your settings in the Security tab. You should not have to perform any manual edits in the console.
Restarting the WebSphere Application Server with Security Activated
At this stage, the WebSphere Application Server is still running without security.
- Stop and restart the WebSphere Application Server.
VERY IMPORTANT: once the WebSphere Application Server is running with security activated, the following command must be used in order to stop it.
On Windows, run the command:
stopServer.bat server1 -user <admin_user> -password <admin_password>On UNIX, run the command:
./stopServer.sh server1 -user <admin_user> -password <admin_password>where
<admin_user>is the name of user chosen to administrate WebSphere, and<admin_password>is the corresponding password. - Restart the WebSphere Administrative Console.
IMPORTANT: the machine name in the URL of the administrative console must include the domain, for example:
http://loug3dsy.dsy.ds:9060/ibm/console/This time, the following dialog box appears:
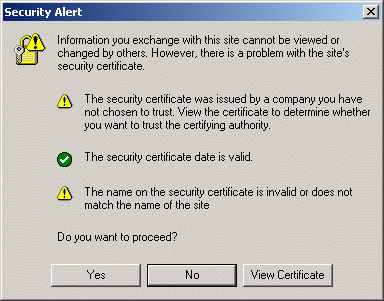
- Click Yes.
This time, the following dialog box appears:
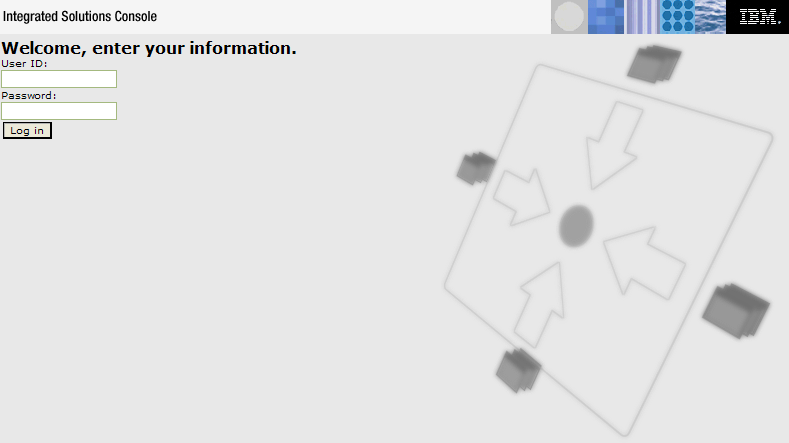
The console appears and prompts you to enter a User ID and Password. These are the Server User ID and Server User Password created earlier using the Security tab.
You are now running a secured WebSphere Application Server using the Server User ID and Server User Password (in our scenario, these are wpsadmin and wpsadmin respectively):
![]()