The topics discussed in this section are:
A route defines a path for sending packets through the Internet network to an address on another network. A route does not define the complete path, only the path segment from one host to a gateway that can forward packets to a destination (or from one gateway to another). There are three types of routes:
Routes are defined in the kernel routing table. The route definitions include information on networks reachable from the local host and on gateways that can be used to reach remote networks. When a gateway receives a datagram, it checks the routing tables to find out where next to send the datagram along the path to its destination.
Beginning with AIX 5.1, you can add multiple routes for the same destination in the kernel routing table. A routing lookup evaluates all routes that match the request then chooses the route with the lowest distance metric. If multiple matching routes have equal distance, a lookup chooses the most specific route. If both criteria are equal for multiple routes, routing lookups alternate choices of matching routes.
In TCP/IP, routing can be one of two types: static or dynamic. With static routing, you maintain the routing table manually using the route command. Static routing is practical for a single network communicating with one or two other networks. However, as your network begins to communicate with more networks, the number of gateways increases, and so does the amount of time and effort required to maintain the routing table manually.
With dynamic routing, daemons update the routing table automatically. Routing daemons continuously receive information broadcast by other routing daemons, and so continuously update the routing table.
TCP/IP provides two daemons for use in dynamic routing, the routed and gated daemons. The gated daemon supports Routing Information Protocol (RIP), Routing Information Protocol Next Generation (RIPng), Exterior Gateway Protocol (EGP), Border Gateway Protocol (BGP) and BGP4+, Defense Communications Network Local-Network Protocol (HELLO), Open Shortest Path First (OSPF), Intermediate System to Intermediate System (IS-IS), and Internet Control Message Protocol (ICMP and ICMPv6)/Router Discovery routing protocols simultaneously. In addition, the gated daemon supports the Simple Network Management Protocol (SNMP). The routed daemon only supports Routing Information Protocol.
Routing daemons can operate in one of two modes, passive or active, depending upon the options you use when starting the daemons. In active mode, routing daemons both broadcast routing information periodically about their local network to gateways and hosts, and receive routing information from hosts and gateways. In passive mode, routing daemons receive routing information from hosts and gateways, but do not attempt to keep remote gateways updated (they do not advertise their own routing information).
These two types of routing can be used not only for gateways, but for other hosts on a network as well. Static routing works the same for gateways as for other hosts. Dynamic routing daemons, however, must be run in the passive (quiet) mode when run on a host that is not a gateway.
Gateways are a type of router. Routers connect two or more networks and provide the routing function. Some routers, for example, route at the network interface level or at the physical level.
Gateways, however, route at the network level. Gateways receive IP datagrams from other gateways or hosts for delivery to hosts on the local network, and route IP datagrams from one network to another. For example, a gateway connecting two Token-Ring networks has two Token-Ring adapter cards, each with its own Token-Ring network interface. To pass on information, the gateway receives datagrams through one network interface and sends them out through the other network interface. Gateways periodically verify their network connections through interface status messages.
Gateways route packets according to the destination network, not according to the destination host. That is, a gateway machine is not required to keep track of every possible host destination for a packet. Instead, a gateway routes packets according to the network of the destination host. The destination network then takes care of sending the packet to the destination host. Thus, a typical gateway machine requires only limited disk storage capacity (if any) and limited main memory capacity.
The distance a message must travel from originating host to destination host depends upon the number of gateway hops it must make. A gateway is zero hops from a network to which it is directly attached, one hop from a network that is reachable through one gateway, and so on. Message distance is usually expressed in the number of gateway hops required, or hop counts (also called the metric).
Interior gateways are gateways that belong to the same autonomous system. They communicate with each other using the Routing Information Protocol (RIP), Routing Information Protocol Next Generation (RIPng), Intermediate System to Intermediate System protocol, Open Shortest Path First protocol (OSPF), or the HELLO Protocol (HELLO). Exterior gateways belong to different autonomous systems. They use the Exterior Gateway Protocol (EGP), the Border Gateway Protocol (BGP), or BGP4+.
For example, consider two autonomous systems. The first is all the networks administered by the Widget Company. The second is all the networks administered by the Gadget Company. The Widget Company has one machine, called apple, which is Widget's gateway to the Internet. The Gadget Company has one machine, called orange, which is Gadget's gateway to the Internet. Both companies have several different networks internal to the companies. The gateways connecting the internal networks are interior gateways. But apple and orange are exterior gateways.
Each exterior gateway does not communicate with every other exterior gateway. Instead, the exterior gateway acquires a set of neighbors (other exterior gateways) with which it communicates. These neighbors are not defined by geographic proximity, but rather by their established communications with each other. The neighboring gateways, in turn, have other exterior gateway neighbors. In this way, the exterior gateway routing tables are updated and routing information is propagated among the exterior gateways.
The routing information is sent in a pair, (N,D), where N is a network and D is a distance reflecting the cost of reaching the specified network. Each gateway advertises the networks it can reach and the costs of reaching them. The receiving gateway calculates the shortest paths to other networks and passes this information along to its neighbors. Thus, each exterior gateway is continually receiving routing information, updating its routing table and then passing that information to its exterior neighbors.
All gateways, whether interior or exterior, use protocols to communicate with each other. Here are brief descriptions of the more commonly used TCP/IP gateway protocols:
Before you configure the gateways for your network, you must first:
The number of gateways you need to configure will depend upon:
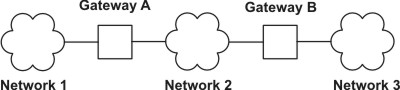
For example, suppose users on Network 1, Network 2, and Network 3 all need to communicate with each other.

To connect Network 1 directly to Network 2, you would use a single gateway (Gateway A). To connect Network 2 directly to Network 3, you would use another gateway (Gateway B). Now, assuming the proper routes are defined, all the users on all three networks can communicate.
However, if Network 2 is very busy, communication between Network 1 and Network 3 might suffer unacceptable delays. Furthermore, if most of the inter-network communication occurs between Network 1 and Network 3, you might want to connect Network 1 directly to Network 3. To do this, you could use an additional pair of gateways, Gateway C (on Network 1) and Gateway D (on Network 3), with a direct connection between these two additional gateways. This may be an inefficient solution, however, because one gateway can connect more than two networks.
A more efficient solution would be to connect Gateway A to Gateway B directly, as well as to Network 2. This would require a second network adapter in both Gateway A and Gateway B. In general, the number of networks you connect through a single gateway is limited by the number of network adapter cards the gateway machine can support.
If your network is small, and its configuration rarely changes, you probably want to use static routing. But if you have a large network whose configuration changes frequently, you probably want to use dynamic routing. You might decide to use a combination of static and dynamic routing. That is, you might want to give static definitions to a few specific routes, while allowing other routes to be updated by the daemons. The static routes you create are not advertised to other gateways and are not updated by the routing daemons.
Choose the routing daemon according to the type of gateway you need and the protocols your gateway must support. If the gateway is an interior gateway, and only needs to support RIP, choose the routed daemon. If the gateway must support any other protocol, or is an exterior gateway, choose the gated daemon.
Note: Unpredictable results can occur if the gated and routed daemons run on the same host at the same time.
To configure a machine to act as a gateway, use the following instructions. For clarity, this procedure assumes that the gateway machine connects two networks, and that the gateway machine has already been minimally configured on one of the networks.
no -o ipforwarding=1
| Task | SMIT fast path | Command file | Web-based System Manager Management Environment |
|---|---|---|---|
| Displaying the Routing Table | smit lsroute | netstat -rn1 | Software --> Network --> TCPIP (IPv4 and IPv6) --> TCPIP Protocol Configuration --> TCP/IP --> Configure TCP/IP --> Advanced Methods --> Static Routes --> Statistics. |
| Adding a Static Route | smit mkroute | route add destination gateway2 | Software --> Network --> TCPIP (IPv4 and IPv6) --> TCPIP Protocol Configuration --> TCP/IP --> Configure TCP/IP --> Advanced Methods --> Static Routes. Complete the following in Add/Change a static route: Destination Type, Gateway address, Network interface name (drop-down menu), Subnet mask, Metric (Cost), and the Enable active dead gateway detection check box. Click Add/Change Route. |
| Removing a Static Route | smit rmroute | route delete destination gateway2 | Software --> Network --> TCPIP (IPv4 and IPv6) --> TCPIP Protocol Configuration --> TCP/IP --> Configure TCP/IP --> Advanced Methods --> Static Routes. Select a route, and click Delete Route. |
| Flushing the Routing Table | smit fshrttbl | route flush | Software --> Network --> TCPIP (IPv4 and IPv6) --> TCPIP Protocol Configuration --> TCP/IP --> Configure TCP/IP --> Advanced Methods --> Static Routes --> Delete All. |
Notes:
- The table is divided into columns for destination address, gateway address, flags, reference count (hop count), and network interface. (For a detailed discussion of each of these columns, see the netstat command in the AIX 5L Version 5.2 Commands Reference.) If frames are not reaching their destination and the routing tables indicate the correct route, one or more of the following conditions might exist:
- The destination value is the dotted decimal address or symbolic name of the destination host or network, and the gateway value is the dotted decimal address or symbolic name of the gateway. (A default route specifies 0 as the destination.)
Routes can be restricted so they can be used only by some users. The restrictions are based on the primary group IDs of users. Using the route command, you can specify a list of up to 32 group IDs that are allowed or not allowed to use a route. If the list is of allowed groups, any user that belongs to any group on the list can use the route. If the list is of disallowed groups, only users that do not belong to any of the groups on the list can use the route. The root user can use any route.
Groups can also be associated with an interface using the ifconfig command. In this case, a forwardable packet can use any route allowed for the groups associated with its incoming interface.
If there are two or more routes to the same destination, any ICMP redirects that are received for that destination will be ignored and path MTU discovery will not be done on those routes.
Beginning with AIX 5.1, a host can be configured to detect whether a gateway it is using is down and adjust its routing table accordingly. If the network option -passive_dgd is 1, passive dead gateway detection is enabled for the entire system. If no response is received for dgd_packets_lost consecutive ARP requests to a gateway, that gateway is considered to be down and the distance metrics (also known as hopcount or cost) for all routes using that gateway are raised to the maximum possible value. After dgd_retry_time minutes have passed, the routes' costs are restored to their user-configured values. The host also takes action based on failing TCP connections. If dgd_packets_lost consecutive TCP packets are lost, the ARP entry for the gateway in use is deleted and the TCP connection tries the next-best route. The next time the gateway is used, the above actions take place if the gateway is actually down. passive_dgd, dgd_packets_lost, and dgd_retry_time can all be configured using the no command.
Hosts can also be configured to use active dead gateway detection on a per-route basis with the -active_dgd flag of the route command. Active dead gateway detection pings all gateways used by routes for which it is enabled every dgd_ping_time seconds. If no response is received from a gateway, it is pinged more rapidly up to dgd_packets_lost times. If no response is received, the costs of all routes using that gateway are raised. The gateway continues to be pinged, and if a response is eventually received, the costs on the routes are restored to their user-configured values. dgd_ping_time can be configured using the no command.
Dead gateway detection is generally most useful for hosts that use static rather than dynamic routing. Passive dead gateway detection has low overhead and is recommended for use on any network that has redundant gateways. However, passive dead gateway detection is done on a best-effort basis only. Some protocols, such as UDP, do not provide any feedback to the host if a data transmission is failing, and in this case no action can be taken by passive dead gateway detection. Active dead gateway detection is most useful when a host must discover immediately when a gateway goes down. Since it queries each gateway for which it is enabled every few seconds, there is some network overhead associated with its use. Active dead gateway detection is recommended only for hosts that provide critical services and on networks with a limited number of hosts.
Route Cloning allows a host route to be created for every host that a system communicates with. When network traffic is about to be sent, a search is done of the routing table to find a route to that host. If a specific host route is found, it will be used. If a specific host route is not found, a network route or the default route may be found. If the route that is found has the cloning flag, 'c', set, a host route for the destination will be created using the gateway from the route that is being cloned. Subsequent routing table searches for that destination will find the cloned host route. Cloned routes have the 'W' flag set. These routes will time out and be deleted from the routing table if they are unused for route_expire minutes. You can modify route_expire by using the no command.
The route cloning feature is used mainly by the path MTU discovery protocol within AIX to allow it to keep track of path MTU information for every destination it communicates with. If the network options tcp_pmtu_discover or udp_pmtu_discover (settable with the no command) are 1, the cloning flag is turned on for all network routes on the system. In AIX 4.3.3 and above, path MTU discovery is on by default.
If you are using the routed daemon, a manually deleted route is not replaced by incoming RIP information (because ioctl's are used). If you are using the gated daemon, and the -n flag is not used, the manually deleted route is replaced by the route as discovered in incoming RIP information.
To configure the routed daemon:
Note: A host that is not a gateway can run the routed daemon, but it must be run in passive mode.
Attention: Do not run the routed daemon and the gated daemon on the same machine. Unpredictable results can occur.
To configure the gated daemon:
Note: Use EGP, BGP, or BGP4+ to advertise addresses of networks in an autonomous system to gateways in other autonomous systems. If you are on the Internet, EGP, BGP, or BGP4+ must be used to advertise network reachability to the core gateway system. Use the interior routing protocols to advertise reachability information within an autonomous system.
Note: The gated version on AIX 4.3.2 and higher is 3.5.9. The syntax of the /etc/gated.conf file has changed. The examples given below are for the 3.5.9 version of gated. To configure the /etc/gated.conf file for versions prior to AIX 4.3.2, use the syntax provided in the /etc/gated.conf file itself.
autonomoussystem 283 ;
egp yes {
group maxup 1 {
neighbor nogendefault 192.9.201.1 ;
neighbor nogendefault 192.9.201.2 ;
} ;
group {
neighbor 192.10.201.1 ;
neighbor 192.10.201.2 ;
} ;
} ;# Send directly to specific gateways
rip/hello yes {
sourcegateways
101.25.32.1
101.25.32.2 ;
} ;
The following example shows the RIP/HELLO stanza in the gated.conf file of a machine that does not send RIP packets, and does not receive RIP packets on its tr0 interface.
rip/hello nobroadcast {
interface tr0 noripin ;
} ;# Perform all BGP operations
bgp yes {
peer 192.9.201.1 ;
} ;To configure the gated daemon to run under Internet Protocol version 6 (IPv6), first ensure that your system has been configured for IPv6 and IPv6 routing:
ifconfig interface inet6 fec0:n::address/64 alias
where
Note: You can use the command netstat -i to see what your IPv6 address is for each configured interface.
If token ring tr0 has an IPv6 address of fe80::204:acff:fe86:298d, you issue the following command:
ifconfig tr0 inet6 fec0:13::204:acff:fe86:298d/64 alias
no -o ip6forwarding=1
ndpd-router -g
See ndpd-router to determine which flags to use for your network configuration.
Starting ndpd-router allows your system to act as a router for the Neighbor Discovery Protocol. Neighbor Discovery Protocol routers inform Neighbor Discovery hosts with routing information so hosts can route IPv6 packets.
Any hosts on the network that you want to be part of the IPv6 network must run ndpd-host. Hosts on the network that run ndpd-host will recognize themselves as part of an IPv6 network and use Neighbor Discovery Protocol, which allows them to determine and monitor link-layer addresses both to allow neighbor routing and to find neighboring routers for forwarding packets.
See ndpd-router, ndpd-host, or read RFC 1970, Neighbor Discovery, for more information.
Next, configure the gated daemon:
Note:AIX 4.3.2 and later run gated version 3.5.9. The syntax of the gated.conf file has changed slightly from earlier versions. Read the gated.conf documentation or use the sample file that is shipped in the /usr/sample/tcpip directory for correct syntax.
When configuring BGP4+ or RIPng, use IPv6 addresses in which the syntax specifies an IP address.
Note: By default, RIPng multicasts its packets.
Once the /etc/gated.conf file has been modified, the gated daemon can be started.
If you use EGP or BGP, you should obtain an official autonomous system number for your gateway. To obtain an official autonomous system number, contact the NIC at INFO@INTERNIC.NET.